I’ve worked in the SOC space for almost 10 years and I find a very strong divide of the end customers:
– We allow the MSSP/MDR access to our network
– We don’t allow them any access, all information requests come through us.
Both are understandable, but it’s more work for the 2nd MSSP when they need to complete a tier 1 investigation. How can automation help?
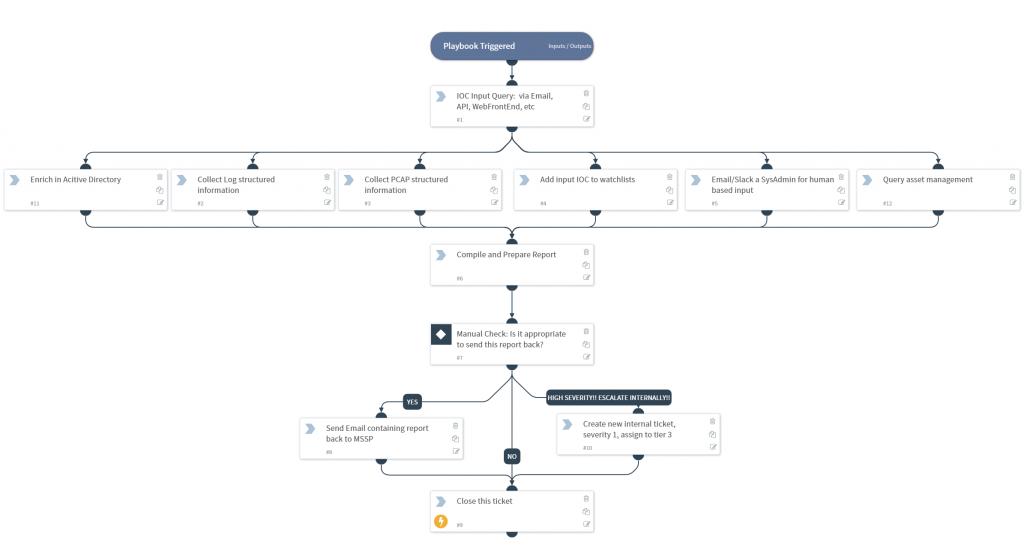
Imagine a SOAR platform inside the customer, that accepts emails [1] from the MSSP/MDR which contains an IOC/attribute. This playbooks then calls out and enriches accordingly….
- Query AD for system owner
- Query Asset Management for context
- Query SIEM for end point alerts
- Query Firewall for logs
- ….and anything else.
The last step in the playbook is to email this report back to the MSSP/MDR, but only after the penultimate check where an end-client analyst reviews the contents first.
This way, with almost no overhead by the end customer, the MSSP/MDR, who still has no access to the network, any usernames, passwords API keys, is able to enrich their own investigation and in-turn increasing value.
Sometimes the simplest playbooks are the best!
Andy
[1] – Email, or maybe a HTTPs front end, validating source IP, with 2FA, etc