I hear this a lot, but it doesn’t matter. If anything, a smaller team has more of a need for SOAR.
Don’t believe me? Listen to Bruce Potter (CISO, Expel) and Mike Johnson (CISO, Fastly) on the CisoSeries blog (fast forward 1m38s)
A listener writes in asking “How do you thrive, and how do you survive as a team of 1?”
The panel discuss many general points, including:
- think about how to amplify yourself
- democratise others to do work on your behalf
- only so many hours in a day for you to get things done
- bring in others to help
- be the architect for security
- think about the bigger picture, of how to apply your knowledge
- find the multipliers
Whilst the panel lean towards distributing responsibilities and finding allies to do work on your behalf (lucky them), I was just hearing:
- Yes, SOAR
- Yes, SOAR
- Yes, SOAR
- Yes, DBot
- Yes, SOAR
- Yes, SOAR
Essentially, automate the hell out of it. If you have 1 or 2 people, surely automation is the only way to scale.
Example: User submits a request (priority 3?), which goes to the bottom of the priority queue, which takes 2 days to find, and 30 minutes to fix. That’s a long wait for something simple. People see the IT team as blockers, not enablers.
Now imagine SOAR performing all those simple/fast requests with a turnaround of 2 minutes. 2 days wait -> 2 mins wait is a 144,000% increase in service you give without any additional head count or training.
Use Cases every sized organisation has to deal with:
- Whitelisting domains
- Joiners Movers Leavers (JML)
- Blocking IP
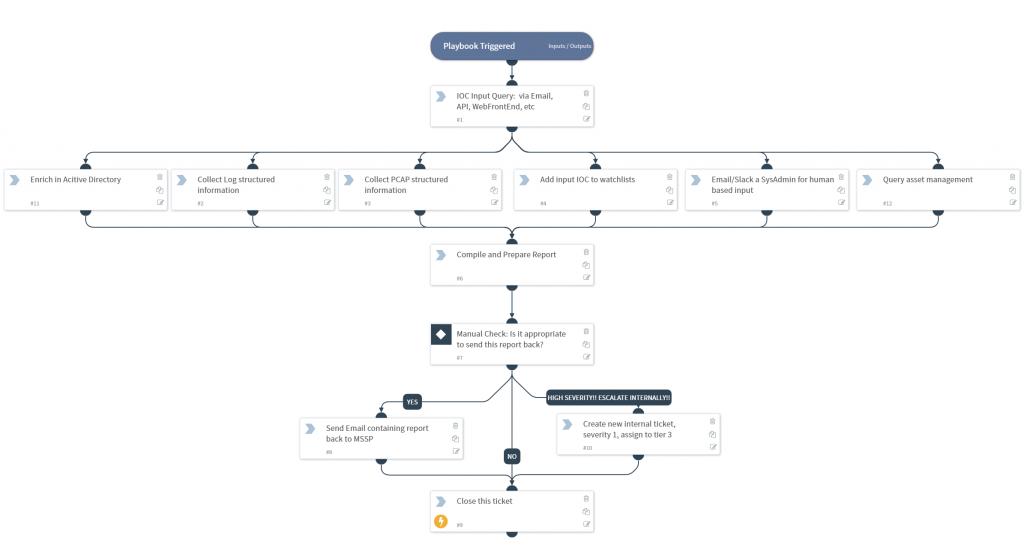
- Enriching IOC for teams
- Phishing
This has a few benefits:
- Smaller ticket queue
- Increased perception of service (your end users feel that your service is always-on)
- More time and less interruptions whilst you are doing more important tasks
That’s just the basics of what SOAR does. Taking that further and using all the functionality of SOAR Case Management here too:
- The remaining 50% of tickets are already prioritised so you wont miss a high priority just because you ‘started at the top of the inbox and worked down’
- Playbooks can interact with non-SOAR users meaning your end users always had the possibility to “click here to escalate this to a security person now” if it can’t wait
- Daily/Hourly reporting to you on the queue size with nice breakdowns on priority, incident type etc.
- Even cooler would be SOAR checking the baseline of tickets. Imagine a security incident happens and many users report a similar issue, if we see this rise we contact you straight away “warning, phishing requests at 205% of normal”
Honestly I could go on lots more on how SOAR in the background supports a smaller team, but I hope this makes the point?
Andy